Risk assessment is a key facet of organizational security.
While some businesses may need to undergo a type of assessment in order to ensure compliance, others may be motivated by the thought of increasing security and safeguarding against threats.
Whichever category your company falls into, performing a risk assessment can be extremely helpful to keep your organization moving forward securely.
This article is meant to outline the general approach your organization should follow to keep secure.
Vulnerability Assessments VS. Penetration Testing
Knowing the difference between vulnerability assessments and penetration testing is helpful when determining where to start your assessment.
Although penetration testing is a helpful tool, it is not always the correct first step based on your organization’s maturity level.
Overall, vulnerability assessments identify issues over their scope, while pen testing shows that those vulnerabilities can be exploited to gain access.
As a result of this difference, pen testing relies on human skills, processes, and tactics and less on automated tools.
What is a Vulnerability Assessment?
A vulnerability assessment generally takes place over a longer time period and consists of looking at specific points in time along the way.
It can be used to identify any trends and changes in security controls.
Vulnerability assessments can also identify possible pathways that could lead to an attack, exploitation, or service interruption using automated tactics.
This is often the lowest cost when it comes to cyber security assessments.
What is Penetration Testing?
Penetration testing involves simulated attacks testing a company’s security measures and serves to confirm the effectiveness of controls put in place to secure these systems.
This type of testing allows for the controlled exploitation of vulnerabilities.
The goal of pen testing is to demonstrate the types of knowledge and skill levels needed to gain access to an organization’s systems, in addition to the path that was taken to gain that access.
These simulated attacks are used to uncover gaps in an organization’s system security.
It’s important to note that pen testing does not negate other paths to gain access and does not invalidate vulnerabilities that may not have been identified yet.
However, it does show what is possible at a specific point in time.
What Should I Know About My Company’s Maturity Level?
The maturity level of your organization plays an important role in determining the type of assessment to pursue first.
The following scale is a helpful method for understanding your security posture and where you might begin.
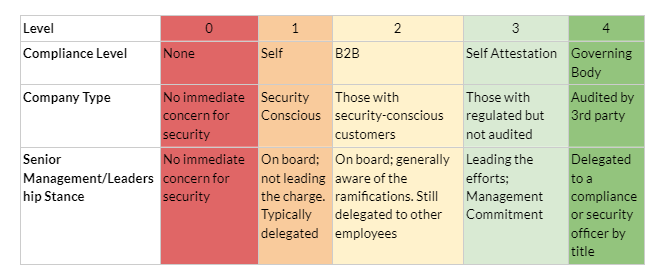
This type of scale is not meant to penalize an organization but is necessary to determine the appropriate testing and assessment tactics.
For example, if a company was considered to be on level 0 according to the scale, it would not be appropriate to start with a penetration test.
Instead, it would be more useful to start with another series of security assessments. This could be a vulnerability assessment or another type to assess the existence of other threats to the organization.
This would ensure the company has the appropriate security activities in place and is building up its security posture before testing the controls.
What are Types of Risk and Security Assessments?
Four types of risk assessments are vulnerability assessments, interpreted vulnerability assessments, penetration tests, and red team testing.
The following table shows the types of risks and security assessments that an organization could undergo.
| Assessment Types | Typical Scope | Results | Cost | Company Maturity Level (applies to) |
|---|---|---|---|---|
| Vulnerability Assessment | Entire network / organization | Report of technical vulnerabilities; not all may be relevant or problematic | $ | 0-1 |
| Interpreted Vulnerability Assessment | Entire network / organization | Report with technical vulnerabilities translated into the actual risk to the organization with remediation recommendations | $$ | 0-2 |
| Penetration Test | Varies from specific system to whole organization | Report on how various combinations of vulnerabilities and exploits were used to gain and maintain access | $$$ | 3-4 |
| Red Team Testing | Organization’s “blue” team | Report on the effectiveness of the controls and responsiveness of the internal security team in thwarting persistent access and lateral movement | $$$$ | 4 |
An organization with a maturity level of 0-2 would most likely begin with a vulnerability assessment, whereas an organization with a higher maturity level could begin with a penetration test or red team testing
Is My Company Well-Protected From Cyber Attacks?
When it comes to security, a layered approach is best to ensure there are other steps in place in case one method is compromised.
Multi-Factor Authentication (MFA) is one example of a layered security approach.
Defense in Depth is another way to think about this. Commonly used in the information security field, Defense in Depth means that an organization does not rely on a single security control but layers of them.
Consider your house as an example.
- 1 Layer: The front door is closed
This is an example of security through obscurity.
Potential “attackers” do not know if the door is locked. They only know that it is closed.
- 2 Layers: The front door is closed, and the standard knob is locked
This still requires the “attacker” to test the door to see if it is locked.
However, they must only defeat 1 additional control to gain access.
- 3 Layers: The front door is closed, the standard knob is locked, and the deadbolt is locked
Adding the deadbolt lock has significantly improved the security posture in this example.
The second layer of the lock requires significantly more effort to defeat.
- 4 Layers: The front door is closed, the standard knob is locked, the deadbolt is locked, and the alarm system is on
Now, we have significantly improved the security posture with the implementation of the alarm system.
The attacker would need to breach a second system entirely in addition to breaching the physical door.
This scenario is similar to the tactics most cyber attackers use.
They search for the path of least resistance, so after finding that the door is locked, most will simply move on.
However, it’s important to note that a motivated attacker will persist, which is a key distinction when scoping an assessment.
Penetration Test Questionnaire
If you believe that your organization is of the appropriate maturity level to pursue penetration testing, reviewing a questionnaire is helpful in determining the scope of the project.
Download our free penetration testing questionnaire so you can get started.
Of course, we’re able to help further if you need an outside organization to help assess your current security protocols.


