A supply chain cyber attack (aka vendor email compromise, or VEC) is an email cyber-attack strategy targeting companies doing business in today’s global supply chain management measured in the tens of billions of dollars a year and growing.
The VEC attack begins with a secret takeover of a valid business email inbox. The hijacker then impersonates that user, ultimately to manipulate and redirect large invoice wire transfer payments to criminal-controlled bank accounts.
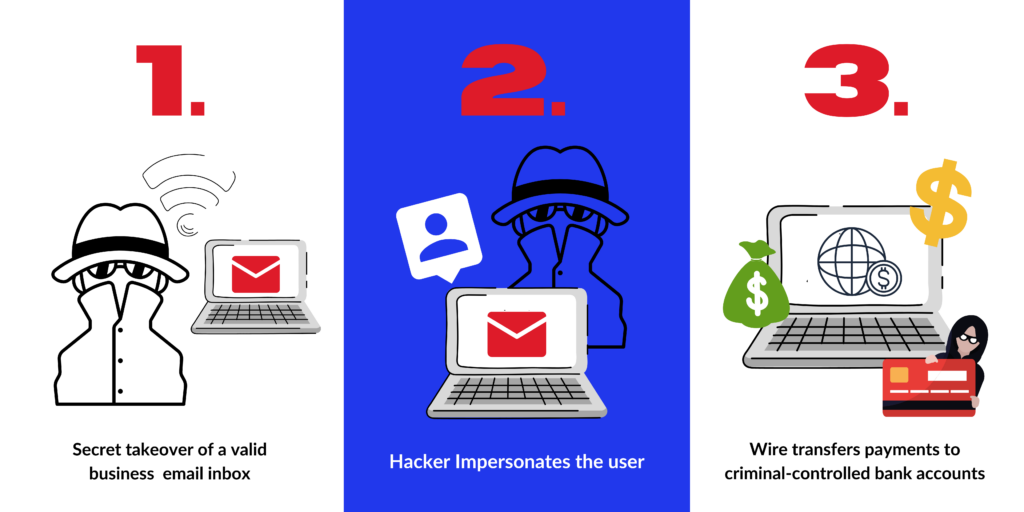
What happens once a vendor email account is stolen?

The thief begins by setting up forwarding rules for all incoming emails so the account holder won’t notice anything wrong.
With unrestricted access to your inbox, they patiently wait for weeks or months, observing and gathering financial intel about the organization—bank accounts, invoicing cadence, employee names/titles.
They use psychological manipulation tactics (aka social engineering), even copying the email writing style of senior financial officers.
The gathered business intelligence enables the bad guys to create realistic emails that can pass as authentic, even under reasonable scrutiny. In most cases, these emails are “from” a senior finance manager directing a subordinate to change bank accounts where invoices are paid.
Criminal networks also use (or sell) a compromised business account as a springboard to launch additional attacks at other companies.
Why are VEC attacks so successful?

The #1 reason: Savvy threat actors target large businesses that regularly work with international wire transfers in large amounts of dollars, euro, yen, renminbi, won, rubles, rupee, pound sterling, etc.
It’s become a more insidious threat today because the global supply chain has stretched to its limits since the pandemic began.
Staggering financial losses
Fueled by the pandemic, vendor email compromise is a more recent specialization within the business email compromise category. Email fraud has been around for as long as businesses have used email as a primary mode of communication between staff, clients, vendors, and financial institutions.

As a measuring stick, look at reported ransomware payment totals for 2020 that clock in at $29 million. The accuracy is unclear because we can only estimate unreported ransom amounts.
Crimes involving compromised email accounts were the most financially devastating type of cyberattack, with nearly $1.8 billion in losses for 2020.
So, why does ransomware still top today’s headlines?
Because as Americans, this crime hits us where we live. Literally. It’s an external attack on our domestic infrastructure.
- Colonial Pipeline (energy)
- JBS USA (food processing)
- Kaseya (small business IT services)
- Numerous agricultural concerns
- Healthcare systems
- City governments
All of which are very high visibility events.
Except for an emerging cyber-attack vector known as killware, all of today’s cyber crime involves monetary gain. Since the pandemic’s start, cyber attacks have dominated headlines with daily reports about new ransomware attacks and strategies.
Ransomware has now evolved to the point that anyone, regardless of technical skill, can become a successful ransomware operator.
So, it’s easy to understand why today’s cyber criminals have invested in ransomware attacks as a source of illicit income. For the smart ones, it’s an easy payday.
What’s the difference between ransomware and vendor email compromise?
The difference is how the bad guys get paid off.
On the surface, both ransomware and vendor email compromise are similar, especially since most ransomware attacks begin with an email phishing lure.
In ransomware, the payment is made voluntarily by the victim to the attackers to unlock encrypted files or prevent sensitive information from being leaked to the public.
Even if a company has the ability to recover from a ransomware file encryption attack, they pay a ransom anyway, if only to avoid corporate embarrassment and preserve brand reputation.
With vendor email compromise, the corporate victim is unaware of the crime until a later accounting audit reveals a dummy invoice payment was wired to a criminal account. The FBI calls this wire fraud.
What is the FBI’s advice to protect your company?

Be careful with what information you share online or on social media. By openly sharing pet names, schools you attended, links to family members, and your birthday, you can give a scammer all the information they need to guess your password or answer your security questions.
Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer provides), and call the company to ask if the request is legitimate.
Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in an account number or payment procedures with the person making the request.
Be especially wary if the requestor is pressing you to act quickly.
How do I report vendor email fraud?
According to the FBI, if you suspect your company has been the victim of an email compromise scam, it’s important to report it ASAP.
- First, contact your originating financial institution immediately and request that they contact the financial institution where the transfer was sent. Sadly, it’s unlikely the money is recoverable.
- Next, contact your local FBI field office and report the crime.
- Then, file a complaint with the Internet Crime Complaint Center (IC3)
What you should be doing to protect your business
The bad guys continue to sharpen their skills and evolve tactics, so we need to stay active in implementing new security measures and training resources.
- Consider an advanced email protection service to keep dangerous emails from ever hitting your inbox.
- Provide ongoing training on how to recognize the most common types of vendor email fraud.
- Have a security policy in place with tighter controls on vendor requests to change an invoice “remit to” bank account.
Together we can prevent compromised accounts and the malicious activity that comes with them.
Stay safe out there.


