SOC 2 compliance plays a pivotal role in communicating and ensuring your organization’s security.
Undergoing an audit allows you to instill trust in customers, vendors, and partners while building up your security posture.
This article will share the significance of SOC 2 compliance, its specific requirements, and the meticulous audit process. Additionally, we’ll delve into the world of pen testing, highlighting its importance in identifying vulnerabilities and fortifying your organization’s defenses.
Gain valuable insights and practical knowledge to safeguard your data and enhance your security posture.
What is SOC 2 Compliance?
SOC 2 (System and Organization Controls 2) compliance refers to standards developed to assess and ensure the effectiveness of an organization’s controls and procedures related to data security, privacy, availability, processing integrity, and confidentiality.
The SOC 2 audit has become increasingly prevalent in cyber security, demonstrating a commitment to data security and privacy. In today’s world, establishing this trust is paramount to your business’ success and ability to differentiate from competitors.
Customers and partners seek assurance that your organization prioritizes the protection of sensitive information and risk mitigation.
This is where the power of SOC 2 compliance becomes evident, as it provides the necessary credibility and peace of mind.

Why is it Important?
SOC 2 compliance holds immense organizational significance;it involves sharing a final report with customers, business partners, and prospects to assure them of the robust controls in place.
This third-party validation instills a profound sense of security in entities seeking to collaborate with your organization.
The comprehensive SOC 2 audit meticulously evaluates your organization’s controls, encompassing security, confidentiality, availability, processing integrity, and privacy.
While the report is non-public, you can share it with individuals deemed appropriate for your business needs.
Rest assured, SOC 2 compliance enables you to showcase your commitment to data protection and engender trust among stakeholders.
Are There Any Specific Requirements?
While there is nothing that mandates, “You must do X in this way,” there are required points of focus that an organization simply must consider.
Management of Risk
The main goal of a SOC 2 audit is to communicate an organization’s commitment to security and effective risk management.
In every SOC 2 audit, demonstrating aspects of risk assessment is required, whether through vulnerability assessments, pen testing, or gap analysis.
Documentation
Documentation is crucial to SOC 2 compliance as it guides auditors on which controls to examine.
For instance, if your documentation specifies password requirements, such as length, complexity, expiration, and history, you must have a group policy that enforces these exact specifications.
SOC 2 recognizes the significance of documentation in aligning controls with audit expectations.
Oversight & Lines of Communication
Effective communication in organizations is twofold, requiring both top-down and bottom-up flows.
This bidirectional communication is demonstrated through tools like org charts, meeting minutes, feedback loops, performance reviews, and documentation sign-offs.
Technical Controls to Enforce the Documented Control Directives
Controls can be directive or require technical enforcement, depending on their nature. The specific technical enforcement varies for each control.
Auditors typically expect “reasonable technical controls” to be enforced during the examination, ensuring compliance.
How Does the SOC 2 Audit Process Work?
Now, let’s dive into the SOC 2 audit process itself.
Audit firms may conduct one or multiple “observation/field visit” meetings throughout the engagement, depending on their approach.
While most artifacts are collected independently, these crucial observation sessions ensure a comprehensive and meticulous assessment, elevating the overall thoroughness of the SOC 2 audit process.
What Will an Auditor Do?
As organizations embark on their SOC 2 compliance journey, it is imperative to comprehend the responsibilities and activities undertaken by auditors.

So, what will an auditor do?
- Inquiry
- Inquiries carry less weight, but they function like a deposition. The auditor may ask if you follow a certain procedure. If you answer “Yes,” this allows them to ask for additional details about your response.
- Inspection – Static
- Observation – Static
- These are similar, but typically, an inspection is by artifact, and observation is by system/configuration.
- Observation – Population & Sample Set
- To demonstrate the “over time” nature of specific controls, the auditor will establish the total and determine how much of that they need to observe to give confidence in the effectiveness of the controls.
The 2 Keys to a Successful Audit
A successful audit hinges on two vital elements that pave the way to a seamless audit experience.
- Actually having and adhering to control activities that your organization will be measured against
- You will have difficulty passing an audit if you don’t have the proper controls in place. As aforementioned, risk management should be accounted for, documentation should be accounted for, and evidence must be able to be collected from systems.
- Keeping all information organized
It’s important to know what systems possess the necessary information and how to transform it into an audit-friendly format. If you don’t know these particulars, it’s vital to consider who does and whether they can help you.
Can You Fail a SOC 2 Audit?
In SOC audits, the absence of a “pass/fail” terminology doesn’t diminish the significance of the outcomes.
SOC 2 provides an objective, independent assessment of an organization’s controls, resulting in one of three opinions: Favorable, Qualified, or Unfavorable.
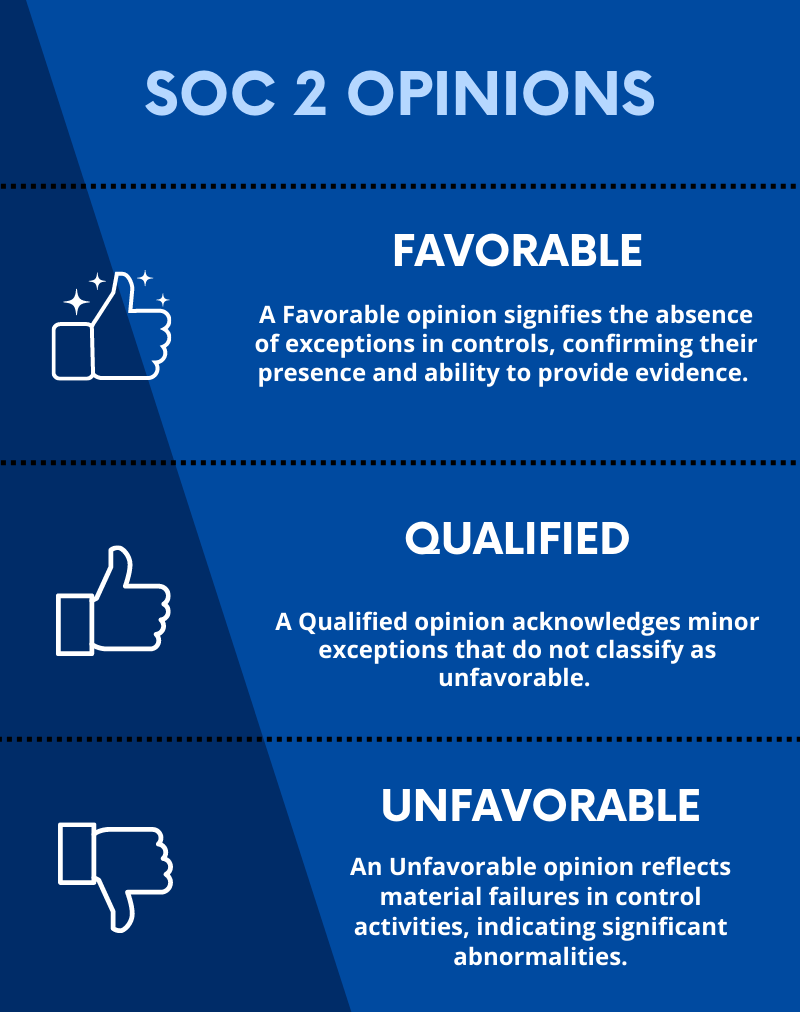
While a SOC 2 audit cannot be failed, an Unfavorable opinion may impact organizational collaborations.
External parties may be deterred from engaging with your company if the audit concerns the absence of specific control activities.
Understanding the implications of audit opinions is crucial, as they shape perceptions and influence potential business partnerships.
What is Penetration Testing?
Penetration testing is a proactive measure that involves simulated attacks to test an organization’s security measures. Its primary objective is to validate the effectiveness of the implemented controls in safeguarding systems and data.
Pen testing reveals the knowledge and skill levels required to gain unauthorized access to an organization’s systems through controlled exploitation of vulnerabilities. It sheds light on the path taken during these simulated attacks, providing valuable insights into potential weak points in system security.
It’s important to acknowledge that pen testing doesn’t eliminate other potential avenues for unauthorized access or invalidate unspecified vulnerabilities. However, it showcases the possibilities at a specific moment in time, highlighting areas where improvements can be made to bolster system security.

Why is Penetration Testing Important?
Penetration testing holds paramount importance in cyber security.
Here are key reasons why it is essential for organizations.
Identifying Vulnerabilities
Penetration testing uncovers potential weaknesses and vulnerabilities in your systems, applications, and networks.
By simulating real-world attacks, it provides a proactive approach to discovering security gaps that could be exploited by malicious actors.
Assessing Defenses
With pen testing, you can evaluate the effectiveness of existing security controls and defenses.
By testing your systems against various attack scenarios, you can measure how well your safeguards hold up and identify improvement areas.
Mitigating Risks
Penetration testing helps you proactively mitigate risks by identifying vulnerabilities before actual threat actors manipulate them.
It allows you to remediate weaknesses and implement more robust security measures, reducing the likelihood of successful cyber attacks.
Meeting Compliance Requirements
Penetration testing is often required for regulatory compliance, industry standards, and certifications.
It demonstrates your commitment to strong security practices and helps you meet compliance obligations.
Building Trust
Regularly conducting penetration testing shows that your organization is dedicated to safeguarding sensitive data and protecting stakeholders’ interests.
This builds trust with customers, partners, and clients who rely on your organization’s security measures.
Overall, penetration testing is crucial in fortifying your security posture, mitigating risks, and instilling confidence in your ability to protect valuable assets and information.
Penetration Testing VS. Vulnerability Assessments
Understanding the distinction between vulnerability assessments and penetration testing is instrumental in determining the optimal starting point for your assessment endeavors.
While penetration testing is valuable, it may not always be the right initial step depending on your organization’s maturity level.
Vulnerability assessments primarily focus on identifying issues within their defined scope, providing a comprehensive overview of potential vulnerabilities.

On the other hand, penetration testing goes a step further by demonstrating the exploitability of these vulnerabilities, showcasing the paths that can be taken to gain unauthorized access.
As a result, if your company has a lower maturity level, starting with a vulnerability assessment might be most appropriate.
With this approach, you can ensure the correct safeguards are in place before testing their effectiveness through penetration testing.
The differences between vulnerability assessments and penetration testing also lead to a divergence in methodology, with penetration testing heavily reliant on human expertise, refined processes, and tactical maneuvers rather than automated tools alone.
This nuanced distinction allows for a more targeted and in-depth evaluation of your organization’s security posture.
By discerning the variations between vulnerability assessments and penetration testing, you can strategically determine the appropriate assessment methodology that aligns with your organization’s needs and maturity level.
Conclusion
We have explored the significance of SOC 2 compliance as a powerful tool for demonstrating your commitment to safeguarding data and building trust with customers, partners, and stakeholders.
From understanding the intricacies of the SOC 2 audit process to unraveling the importance of pen testing, you should now have the right knowledge to fortify your organization’s defenses in the digital world.
By embracing SOC 2 compliance and implementing robust security measures, you can pave the way to a successful and secure future.
Visit our Cyber Security and Compliance guide for further exploration and an in-depth understanding of these topics.


